SIM cards are not only small chips for making phone calls. In fact, they carry a lot of personal information about their owners which can be very serious if the wrong person had them. SIM card theft is a common way of identity theft thieves may use to access your personal data. Even more, they can access your financial information and use them without your consent. If a thief had your SIM card, there are a lot of things he can do with it. So, let’s understand the risk of sharing contact information or related issues and how to prevent that.
Consequences of SIM card theft
Basically, having your SIM card allows the person to insert it into any other phone and access your accounts linked to your number. Also, he can make calls and send messages impersonating your identity. That’s not all, strangers can do more things when having that small piece of cellular technology, like the following ones.
Using your number
The thief can use your SIM card to make calls and send messages without paying for them. Simply because the SIM card is registered with your name, and there is no evidence you didn’t make these calls. Similarly, he may access the internet and use cellular data to browse whatever content is on the internet without paying a single penny. So, he will use it for his own personal use and you have to pay the bills. If it’s a prepaid number, then, the person won’t use more than what’s included as a data limit.
Other than that, the person may try to make pranks with your contact number, and that may cause issues for others like friends or family members. Also, the problem may be a little complicated when that SIM has the contact list.
Impersonating your identity
With your SIM card and little information about you, the thief can call your bank or card issuers, for example pretending to be you, and get more information. Later, he might use this information to do other transactions with your financial information.
In addition, you may have some dating accounts or social media profiles linked to that number. So, imagine if someone has access to that platform and tries to reset your password. Consequently, the app will ask for the associated cell number which the person has to receive the verification code by SMS. Of course, that won’t be as easy as it looks for a stranger to do all that, but some social media networks have weaknesses in their security and profile validation algorithms.
Access two-factor authentication
Most online services now use two-factor authentication methods for more security. This is by requiring a password and a passcode sent to your phone number every time you use their service. With your SIM card, thieves will receive two-factor authentication codes and can use them to access some of your accounts on Facebook, Instagram, etc…
Further, they can sign up for any service using your credentials (assuming they know them). Then, confirm your identity with the text code sent to your number.
How it occurs?
SIM card swapping. The most common way that doesn’t need any technology for stealing chips is called SIM card swapping. Simply, thieves will call your cellular service provider pretending to be you and report their SIM card is lost or not working. Next, he will ask for a replacement sent to his address. That way, they have a copy of your chip even without touching your mobile phone.
In some cases, phone providers like in the US will ask for some personal information before sending any replacement SIM cards. So, if the thief managed to hack or steal some of your personal identifying information, he will do this SIM card swapping easily.
SIM card cloning. Cloning is similar to swapping in the effects but the method is different. In SIM cloning, the thief must have access to your original SIM card to clone it. So, it is more difficult than SIM card swapping. The thief has to take your microchip and create a clone of it using certain software. This software will produce an exact copy of the SIM card including all the information stored on the SIM.
With this copy, the attacker can have access to your accounts and authentication codes. Then, he will use this information to impersonate you on social media like TikTok, YouTube, and Snapchat, or do transactions with your name.
How to avoid the consequences of SIM card theft?
Although it is hard to prevent SIM card theft (unless by refusing to give your mobile phone to anyone), you can mitigate some of the resulting risks. Even if a thief managed to do a SIM card swap, you can avoid most of the identity theft attacks he might do.
Hide your personal information
In most SIM card swaps, thieves need to know your basic personal information in case customer support asks for it. So, if you manage to hide this information from anyone you don’t know, there is a big chance they won’t be able to do the SIM card swap.
Also, even if they managed to do so, they still need some information to steal your bank IDs, credit cards, and others. Thus, try not to write much about yourself as your address or phone number on social media or any other online platforms.
Use multi-factor authentication
Instead of using two-factor authentication only, use a multi-factor authentication system. This requires other authentication codes rather than the one sent to your phone number. For example, you have to write a password, the code sent to your phone, and a code that appears on the authentication app. Using this method, even if the thief has access to your SIM card, he won’t be able to provide other codes.
SIM PIN
Nearly all mobile phones have the feature of locking your SIM card with a PIN code. Hence, if anyone attempts to use the SIM card, he has to provide this PIN code. The PIN code is provided by the SIM card provider not you. However, you can change it later but you need to get the original PIN.
To activate the SIM PIN lock on iPhone or Android, go to settings and search for that option. On iPhone for example, you can find that under the cellular option as in the next screenshot.
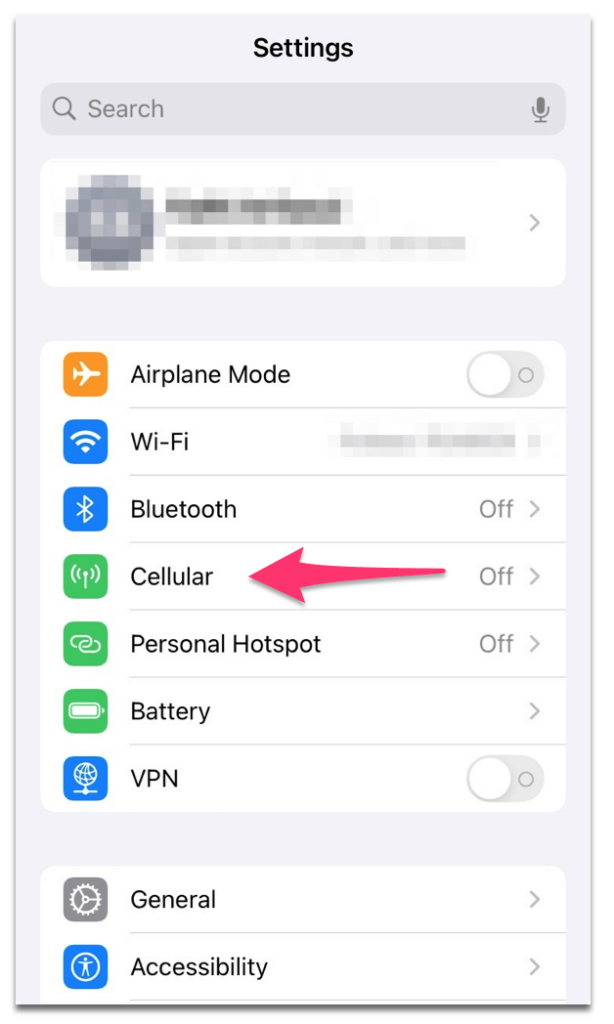
After that, scroll down a little bit to find the number you have. Tap on it to get the options, and you see the PIN activation in the next screen to activate it.
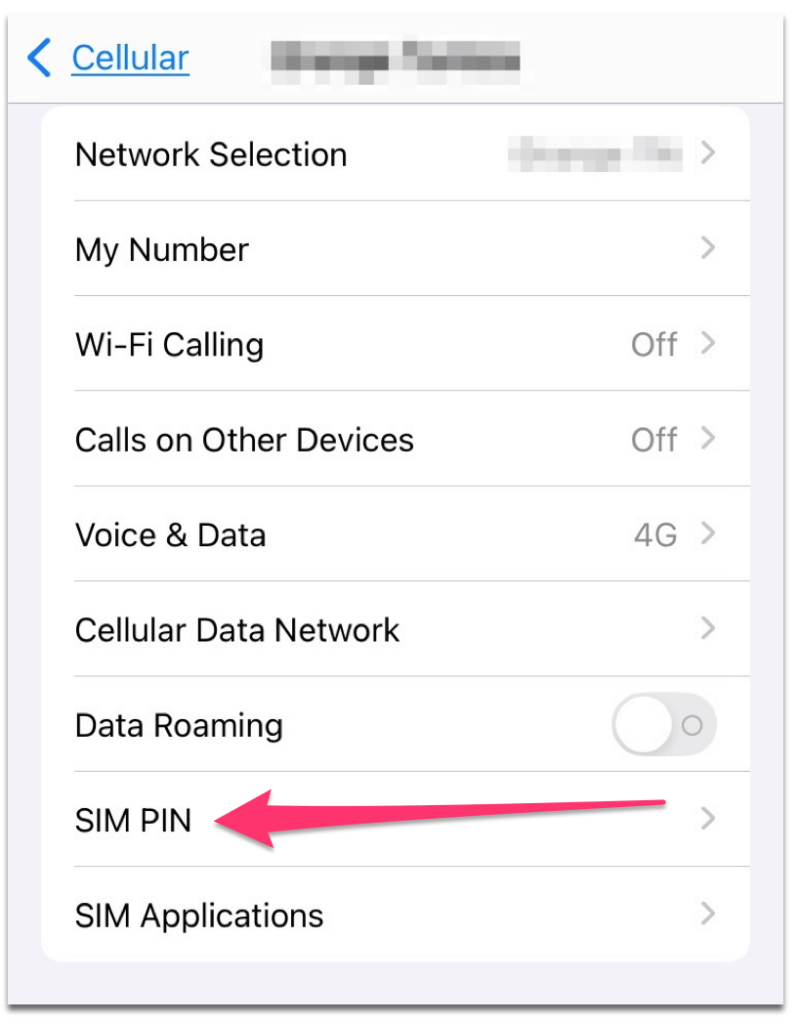
Now, write down the original PIN lock you got from the SIM card provider. Next, change it or just use this original one.
One last thing to mention here is that if you received any suspicious text messages as authentication codes you didn’t request, contact your cellular provider. Similarly, if you feel your call or data package is consumed fast, check your consumption or contact customer support. Ask for a detailed consumption report to see if someone else is using your SIM card or not. If yes, cancel your chip immediately.
Although SIM cards don’t seem to hold much information, they can be used to get access to sensitive personal information. A SIM card attack can lead to other costly and sometimes very serious consequences. Thus, consider all the security features available for you to protect yourself from such an attack.